
Web Commodore Digital Proof
Register and protect your digital assets
Create Digital Proof
Digital ProofVerify Digital Proof
VerifyCreative Works Designs & Plans Research Data Trade Secrets Contracts & Documents Digital Assets Data Logs

Proof of Existence
Web Commodore Digital Proof Tokens are timestamped evidence of the existence and your possession of any digital file, registered on the GoChain public blockchain

Safeguard Digital Assets
Evidence that digital files were in your possession at a specific point in time to safeguard against misuse and misappropriation - without disclosing their contents

Indisputable Evidence
Our timestamped proof tokens of your digital assets are admissible as evidence in court as Web Commodore retains the full chain of custody.
The easiest and quickest way to register ownership of your digital assets and creations on the public blockchain
Web Commodore Technology

Digital Proof Token Encryption
Web Commodore Digital Proof Tokens are generated using a locked-down Hardware Security Module (HSM) certified to FIPS 140-2 Level 3 standard for all cryptographic operations

Trusted Time Stamp
Web Commodore is a trusted Time Stamping Authority (TSA). All Digital Proof Tokens are signed in accordance with the IETF RFC3161 industry standard with a date and time stamp accurate to within 3 milliseconds, synchronised to the Coordinated Universal Time (UTC)

Digital Proof Token Security
Web Commodore uses security standards-compliant systems for all its operations and uses a private RSASSA-PSS 3072 bit security key locked down in a FIPS 140-2 Level 3 HSM module to sign all Digital Proof Tokens. Digital Proof Tokens are registered as non-fungible tokens (NFT) on the GoChain public blockchain.
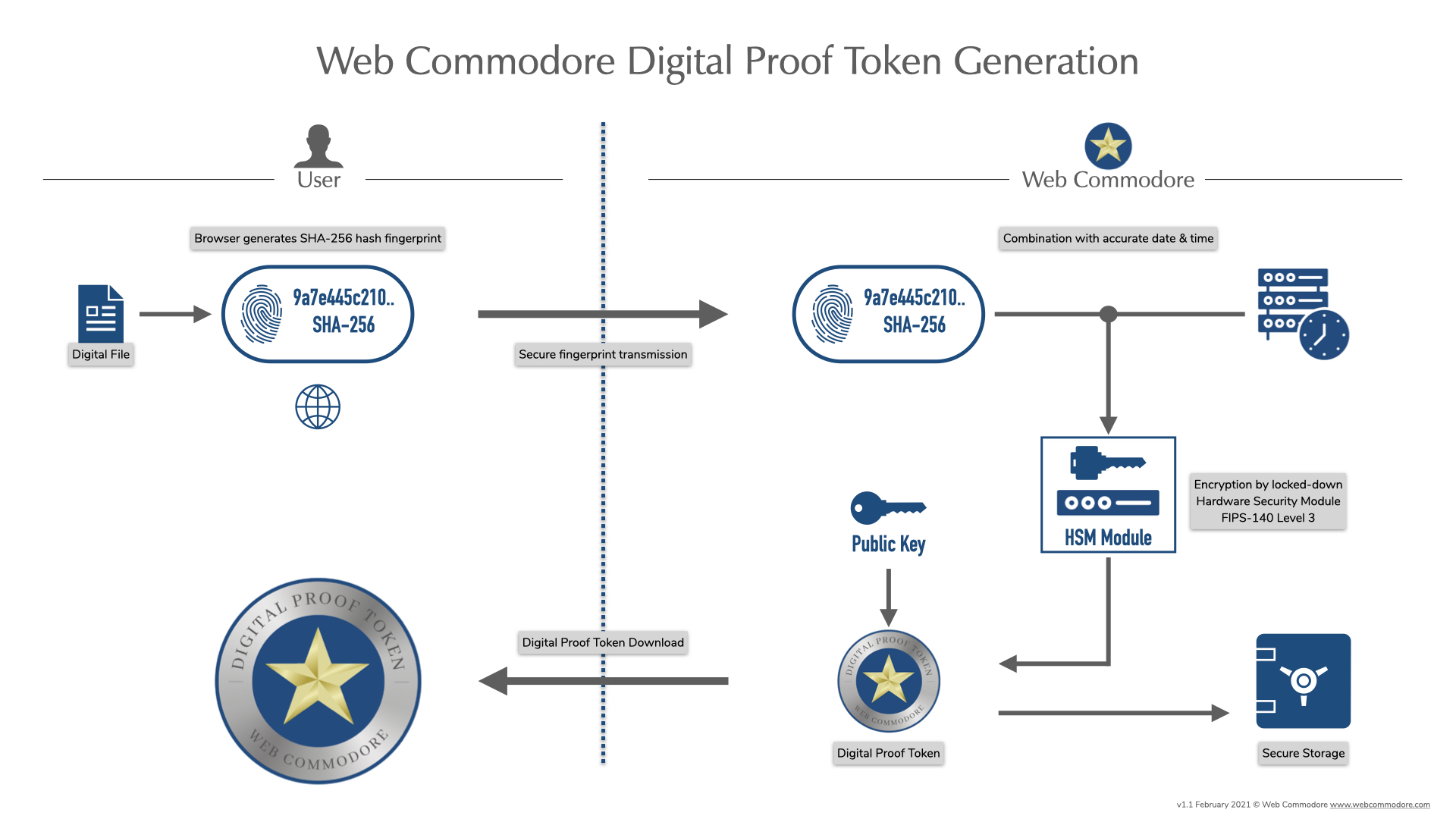
1A unique fingerprint (sha-256) of the digital file is generated by the browser and transmitted to Web Commodore.
2The fingerprint is combined with an accurate timestamp.
3The fingerprint / timestamp combination is encrypted using a locked-down Hardware Security Module (HSM)
4Together with a public key to provide authenticity, this generates a Digital Proof Token
5The Digital Proof Token is registered on the GoChain public blockchain
6The ownership and integrity of the digital file can be verified at any time
 Digital Proof Token[Plain text / 3KB]
Digital Proof Token[Plain text / 3KB]
Digital Proof Certificate[PDF / 1.3MB]
Latest Web Commodore Blog Posts
Digital Proof

How Non-Fungible Tokens (NFTs) Can Help Digital Creators Prove Ownership
We live in a world of online sharing and collaboration. Digital creations are shared with fans, co-workers and customers with a simple mouse click or finger tap, giving all recipients instant access to the digital works itself. The internet has made the distribution of any digital creation super-effective. Where it lacks efficiency, however, is in the area of ownership and rights protection. Particularly in the context of collaborative projects, take for instance the production of a music video, numerous individual digital assets form the ingredients. Photos, music creations and recordings, and video clips containing footage that may or may not actually make it into the final production are shared and submitted by collaborators. Formal registration of ownership and copyright tends to be reserved for the final product only, leaving the "ingredient" digital works relatively unprotected.
Continue reading
Do You Need Help Protecting Trade Secrets?
Regardless of the industry you work in, there are always going to be trade secrets - confidential information such as documentation about processes or algorithms, a business plan, a client list or competitive intelligence. Should such information ever fall into unauthorised hands, you may not be able to claim damages unless you can prove that the confidential data was in your possession in the first place. In itself, the requirement to evidence your trade secret history appears to contradict the imperative of how confidential information needs to be treated: To keep it secret.
Continue reading
Proving Your Copyright: Can You Date and Timestamp Your Work?
Whenever copyright disputes and claims arise, there is always one issue which emerges – the matter of date and time of creation. While one party can claim against another if they protest they are copying their intellectual property, they will always need to make sure they have appropriate proof to show that they can back themselves up.
Continue reading







 Blockchain Registration Details
Blockchain Registration Details